Uncover and mitigate cybersecurity risks with full-scale penetration testing
Mitigate cyber threats, and close the gaps in your cybersecurity with a modern approach to penetration testing that automates and simplifies your pen testing process.
A modern approach to penetration testing
You can have market-leading cybersecurity solutions in place, but it's the things you're unaware of that can hurt you the most.
Enabl's modern Penetration Testing helps you uncover the gaps in your cyber defences and close them before they result in a data breach. Our Penetration Testing is a full-scale service that utilises an array of information discovery, exploitation, password cracking and penetration tools to deliver comprehensive White Box and Black Box Penetration Testing.
Many businesses see Penetration Testing as an expensive, compliance-related tickbox they need to check, often opting for a once-a-year test. We're flipping this on its head, with our Penetration Testing service helping businesses perform regular, ongoing Penetration Testing at any time, for a cost that's often less than the one-off test. You'll also receive real-time reports, preliminary findings, and notifications through our live portal.
Traditional Penetration Testing
-
One and done - point in time assessment of cybersecurity strength.
-
Long turnaround time - reports and other deliverables have longer turnaround time (approx. 2 weeks on average)
-
Charges for subsequent tests - assessing the impact of any remediation efforts may require additional paid tests
-
Varied methodologies - penetration methodology executed may vary consultant-to-consultant based on experience and memory
Our Modern Pen Testing Service
-
On-going penetration testing - access regular penetration testing with up-to-the-minute risk identification
-
Real-time live dashboard - access live reporting data, identified threats and notifications on any risks through our customer portal
-
Free re-test post remediation - we'll re-test your security post-remediation and provide insights on the impact of the changes made.
-
Compliance with frameworks - pen testing taks based on MITRE attack framework and internally built framework by OSCP and OSCE certified consultants
The growing importance of penetration testing
%
Of organisations tested had at least one medium, important or critical vulnerability
(Source: Vaadata)%
Of successful perimeter breaches were achieved using vulnerable web applications
(Source: Kaspersky)Our penetration testing services
White Box
White Box penetration testing provides the tester full, open access to your system's source code, network architecture and other key documentation. The tester takes an inside-out approach to identifying vulnerabilities.
We'll comb through large volumes of data and documentation for vulnerabilities, analyse source code, debug software and use a range of tools to minimise the chance of missing a vulnerability.
Our White Box Penetration Testing includes:
- Informational gathering
- Vulnerability discovery and validation
- Exploitation and post-exploitation
Black Box
Black Box penetration testing sees the tester assuming the role of a cybercriminal with limited knowledge of the targeted system. The tester lacks detailed internal information like architecture diagrams or source code.
Acting as an external threat, we'll look to find vulnerabilities from outside the network, simulating common techniques used by cybercriminals in an attempt to breach the system.
Our Black Box Penetration Testing includes:
- User profiling and reputational threat analysis
- Informational gathering
- Vulnerability discovery and validation
- Exploitation and post-exploitation
Post-Test Remediation
What do you do once we've identified a vulnerability? Our penetration testing services include recommended remediation strategies and a remediation roadmap. All the information you need to close the gaps in your defences.
We can even execute these remediation strategies on your behalf, saving you time and providing peace of mind that any vulnerabilities have been taken care of.
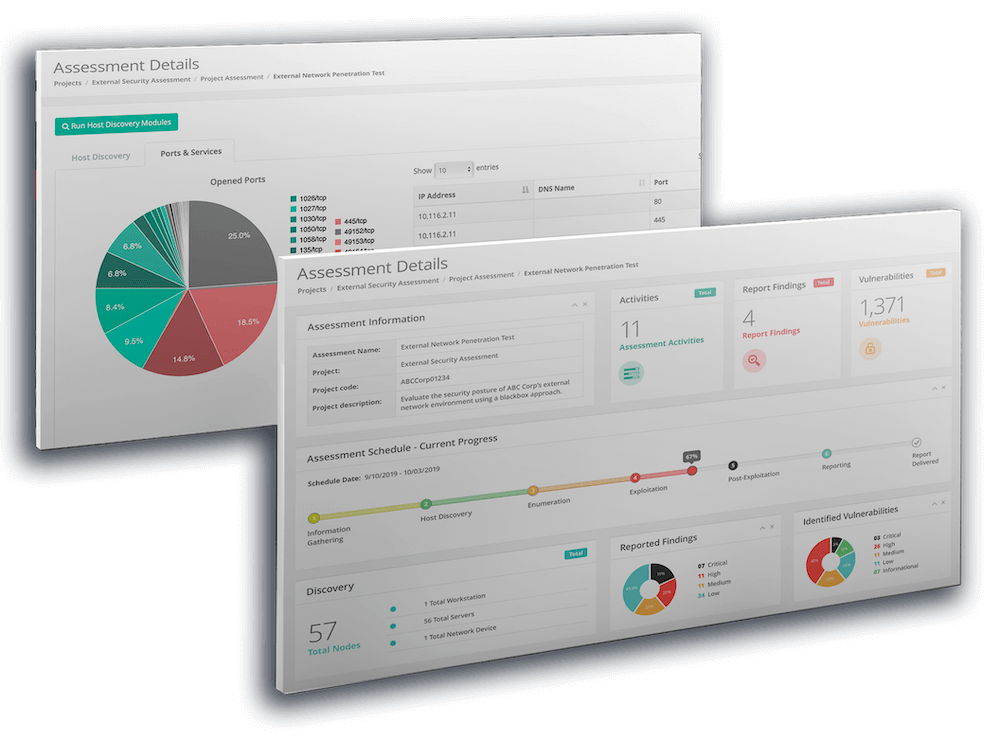
Uncover your cybersecurity vulnerabilities in real-time
How long did you wait for a report and remediation the last time you performed a penetration test? Were vulnerabilities left for days while your provider completed their testing?
Our modern penetration testing service gives you access to a sophisticated online portal to manage and view the results of your penetration tests. You can take control of your vulnerabilities quicker and with less back-and-forth communication.
Run tests regularly
Conduct full-scale penetration testing at regular intervals with ease. Don't get stuck waiting around for someone to respond to you, access vulnerability reports when you need them.
Real-time notifications
Stay informed throughout the entire penetration testing process. Receive high-priority notifcations of any vulnerabilities found.
Actionable reporting at your fingertips
FAQs
What is Penetration Testing?
Penetration testing, often referred to as pen testing, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. It's vital for businesses because it helps prevent data breaches by identifying and allowing you to address security weaknesses before they're exploited by malicious attackers.
How often should penetration testing be performed?
The frequency of penetration tests can vary depending on several factors, such as changes to infrastructure, compliance requirements, or after significant upgrades and modifications. However, it's best practice to conduct pen tests at least annually to ensure consistent network security and data protection.
Enabl's modern penetration testing platform provides access to on-demand penetration testing, so that you can regularly test and remediate throughout the year.
What is the difference between white and black hat penetration testing?
White hat penetration testing, also known as ethical hacking, is authorized testing performed by cybersecurity professionals who use their skills to identify and help fix vulnerabilities within a system. These professionals follow a code of ethics, ensuring they work transparently and with permission.
Black hat penetration testing, in contrast, refers to unauthorized and malicious hacking. Black hat hackers seek to exploit vulnerabilities for personal gain or to cause disruption, without the consent or knowledge of the system owners. The key difference lies in the intent and authorization behind the testing - white hat tests aim to improve security, while black hat activities are criminal actions against it.
How long does penetration testing take?
The testing time varies based on your network size. Usually, our penetration tests take 1-4 days to run a full test and vulnerability scan. Reports and deliverables are ready within 2 days after the assessment.
How much does penetration testing cost?
The cost of pen testing can vary widely based on scope and provider, ranging from $5,000 - $50,000.
Enabl's modern penetration testing offers competitive pricing compared to traditional pen tests, and provides much more value for a similar price point through:
- Included post-remediation testing
- Access to live data and reporting
- On-demand pen testing
Identify your vulnerabilities
Need to find and resolve your cybersecurity vulnerabilities? Let's talk.
