9 Common Types of Phishing Attacks and How to Spot Them

Contents
Phishing attacks are among the most common threats that companies face. 83% of businesses have experienced phishing attacks in the past. And 36% of data breaches involve phishing.
The major challenge of protecting your business from phishing comes down to the fact that you're relying on your people's cyber awareness and ability to spot a phishing attempt. But not every employee in your business is a tech wizard and their cyber-savvy differ from person to person.
Combine this with the fact that phishing attempts are getting trickier, with new tactics being employed, they can be harder to spot. But we've got your back - we've compiled the main types of phishing attacks that your business should be on the lookout for.
Types of phishing attacks to watch for
Statistics show that human error is one of the leading causes of cyber breaches. According to a report by the World Economic Forum, 95% of cybersecurity issues are due to human error.
Why is this so? Well, humans are fallible—we make mistakes. We can be tricked, manipulated, and even coerced into acting against our best interests or those of our organizations. This susceptibility makes us prime targets for cybercriminals who exploit human weaknesses to gain access to systems and data.
1. Spear phishing
These are personalized attacks designed with a specific company or group in mind. They're cleverly crafted to appear genuine, making it alarmingly easy for unsuspecting victims to click on malicious links. These attacks often use inside information about the target organization to increase their appearance of legitimacy. The attacker might, for instance, pose as a trusted colleague or partner, making it harder for the recipient to spot the deception. It's a growing concern, especially for businesses that handle sensitive data.
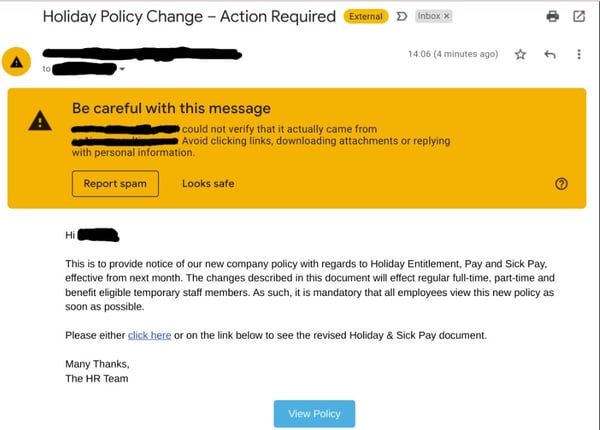
2. Whaling
This type of phishing attack zeroes in on high-value individuals, like senior executives, who possess access to sensitive company information. The cybercriminals behind these attacks often take time to research their targets, leading to highly personalized and convincing scams. Their goal is to trick these influential individuals into revealing confidential information or approving fraudulent transactions. The potential damage from these attacks can be substantial, given the level of access these individuals have within their organizations.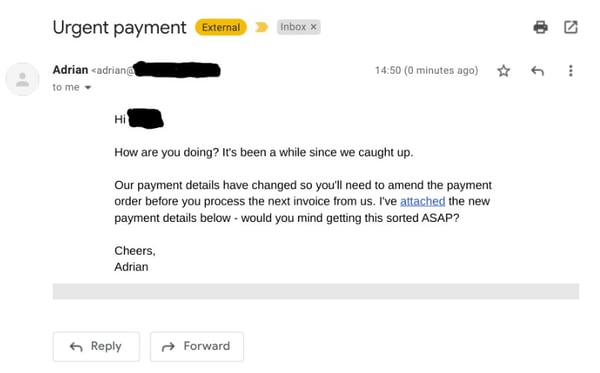
3. Smishing
Have you ever received a suspicious text message with a link to an unknown website to update your details? Maybe you've received the Australian classic AusPost failed delivery scam messages? That's smishing. It leverages the inherent lack of sender domains and branding in text messages to deceive recipients into sharing sensitive information. Because text messages are typically less scrutinized than emails, many people fall victim to these scams. Remember, always question unexpected or unusual text messages, especially those asking for personal details or directing you to follow a link.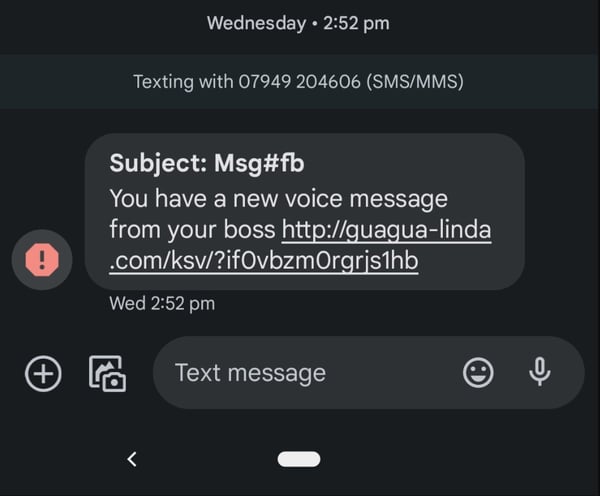
4. CEO Fraud
In this insidious scam, a cybercriminal poses as the CEO and directs an employee to carry out a fraudulent action. The perceived authority of the CEO makes these scams particularly effective. Employees, eager to respond promptly to a request from the top, might not take the usual precautions before following the instructions. This type of fraud can lead to significant financial losses and damage to a company's reputation.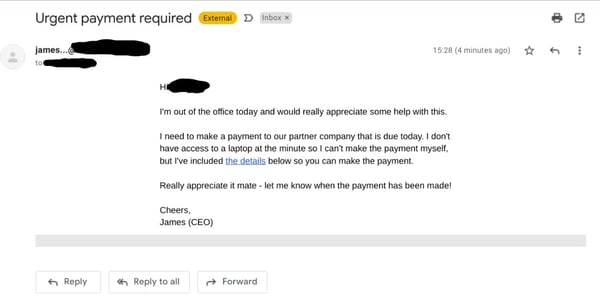
5. Business Email Compromise (BEC)
Here, the attacker impersonates a business partner or vendor. These scams often involve intricate research and long email threads to appear genuine. The attackers typically insert themselves into existing email conversations or start new ones, persuading the victim to make a payment or reveal sensitive information. Because they appear to come from trusted sources, these scams can be particularly difficult to detect.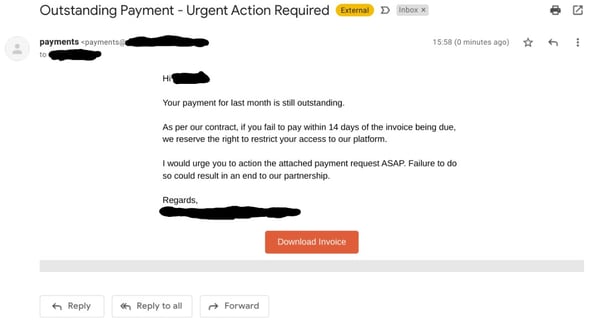
6. Vishing
This is voice-based phishing, where the attacker calls the victim, posing as a partner firm or supplier, to extract sensitive information or request a payment. These calls often seem legitimate, with the caller using professional language and referencing seemingly accurate details about the victim or their company. Like other forms of phishing, the key to avoiding vishing is scepticism: always verify unexpected or unusual phone calls before revealing any confidential information.
7. Pretexting
Also known as socially engineered phishing, pretexting involves crafting a believable narrative or 'pretext' to trick the victim into sharing confidential information or making a payment. The attacker might pretend to be a tech support representative, a police officer, or even a fellow employee. The story is designed to provoke an emotional response, pushing the victim into taking action without thinking. Always remember, if a call or message seems suspicious, it's better to double-check than to regret it later.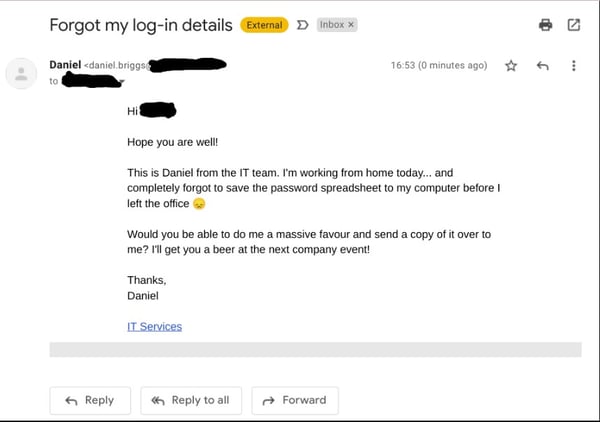
8. Angler Phishing
This type of phishing attack takes place on social media. The attacker impersonates a brand's customer service agent to engage with users and steal their personal details. They might respond to a customer's tweet or comment, offering "help" that ultimately leads to fraud. It's yet another reminder to be vigilant online – always verify the identity of customer service agents and be wary of providing personal details over social media.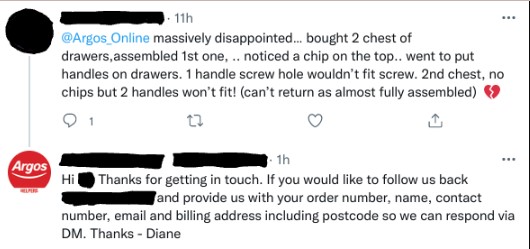
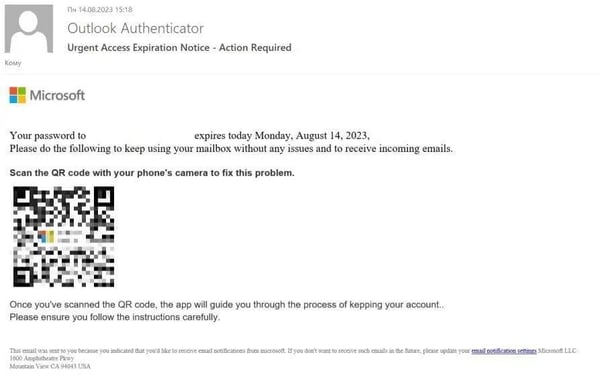
9. Quishing or QR Code Phishing
Quishing or QR code phishing is becoming more common with the prevalence of QR codes. Cyberattackers will create deceptive QR codes that appear legitimate but lead to phishing websites or prompt the user to download malicious data to their device. These QR codes can be found on posters, flyers, and even in the digital realm.
How can you protect your business?
With phishing attacks becoming more sophisticated and prevalent, it's crucial to take measures to safeguard your business. While technical solutions like spam filters can help reduce the number of phishing emails reaching users, they can't catch everything. That's where addressing the human factor comes in.
Here's a three-step approach to bolster your defences:
- Education: Equip your team with knowledge. Teach them about the risks of phishing and how to spot suspicious emails. However, educating your team about phishing isn't a one-time event. Cyber threats are constantly evolving, with new tactics and schemes emerging regularly. As such, your team's training should be continuous and regular to keep up with these changes.
- Testing: Put your team's learning to the test with simulated phishing exercises. Simulated phishing is a proactive approach where you send fake phishing emails to your own team to see how they respond. This mimics real-life scenarios and tests their ability to identify suspicious emails, links, or requests.
- Culture: Foster a security-first culture. Encourage your team to prioritize security and ask questions when in doubt. A survey reveals that 40% of employees might conceal a cybersecurity incident they're responsible for due to fear or embarrassment. This behaviour can lead to undetected breaches, giving cybercriminals more time to cause damage.
Worried about susceptibility to phishing? Get your FREE Human Risk Report
If you're worried that your staff may not be able to spot a phishing campaign or that you may already have employee details leaked on the dark web, we can help you uncover this information via a Human Risk report. Get in touch below to access your free report.
